As a digital nomad, my laptop and phone are basically my hammer and nails…my easel and brush…they are the tools by which I make my living, and the portal through which I am able to research, imagine, arrange, strategize and coordinate both my professional affairs, and all of my travel.
There’s only one problem…
They’re HIGHLY susceptible to all sorts of thievery, plundering, pillaging, destruction, eavesdropping, hackery and tom-foolery.
These days if someone steals the information on your phone or computer…they’ve essentially stolen your life.
For a moment let’s set aside the philosophical problems I should (and do) have about how addicted and indentured I am to technology…
And let’s just admit that most of us have the same problem. We are susceptible to cyber crime more now than ever, because we use technology to interact with our work AND our friends more than ever in the history of the universe.
You wouldn’t walk through dangerous crowded unknown territories littered with thieves, robbers, pirates and attackers without taking as many precautions as possible to avoid, thwart, or deter them, would you? (Actually…sometimes I would…but that’s beside the point)
So why should you connect to the internet…the biggest den of thieves ever invented…completely blind, unprotected, unaware and begging to be pick-pocketed, spied on, attacked and compromised?
Luckily for you…there are some simple steps you can follow that will shield you from the would-be attacks of the internet’s scoundrels, scalawags, and ne’er-do-wells.
Disclaimer: I’m no security expert, so I’m making no guarantees here. But, I do everything I can to protect myself and I have been a techie for the better portion of my life, so I do have a pretty firm grasp on the concepts. For more advanced knowledge, check out Future Crimes by Marc Goodman, or a free podcast called Security Now on the TWIT network.
Rest perturbed…if someone REALLY wants to hack your stuff and steal your information…they almost certainly can find a way.
But just like you would avoid the scarier parts of a city, walk in well-lit areas and carry locks on your bags to deter thieves in a new city, you can make it not worth most hackers’ time to get to your information by following these few rules.
The 3 Steps To Secure Your Laptop and Phone While Traveling…
Step 1: Let Go (Pre-Emptive Mourning)
The first step to protecting your digital information, data, and devices is actually more of a mental exercise. The easiest way to live without fear of theft, privacy hacking or being compromised…
Is to accept that it will happen. Or at least…that it very likely COULD happen.
Take time to really…deeply…vividly…imagine what will be the absolute worst case scenario if it happens. If someone steals your identity…if someone hacks your password…or if you happen to leave your brand new $2,500 macbook air on the london tube on your first day of the trip like I did back in 2012…
Will you lose money?
Will your private photos get shared with one or many people?
Will your private documents for your business or the company you work for become compromised?
Could this lead you to lose your job? Or your business?
Just imagine the most hellish, irreparable possible situation that will happen to you if you lose your laptop, phone or tablet. Sit in that visualization for a few moments. Maybe it would help to write down all the worst things that could happen.
Then realize…that it won’t be that bad.
If you lose your job (which probably won’t happen)…you’ll find a better one, or finally get that push to start something of your own…
Work through each of the possible nightmare outcomes and keep asking (write the questions and the answers preferably)…
“Why am I afraid of this?” or “What’s the most likely outcome if this happens”
You’ll quickly realize whatever you’re afraid of probably isn’t that bad.
And it’s better that you have this conversation with yourself now, than when you suddenly get blindsided.
If you can accept that your digital property and devices can and very probably will at some point get stolen, tampered with, or hacked, then you can relax…
Maybe have yourself a good cry imagining the “death” of your photos…your music…your data…and your precious macbook (like I did)…
And then you can relax, and get to work implementing Step 2…
Step 2: Mitigate Your Losses (Redundancy)
These days it’s easier than ever with “the cloud” (in all of its mad incarnations) to make sure that all of your most important information is always backed up, secured, and easy to recover.
If you’re not taking advantage of this…well, it’s your fault when something bad happens.
The #1 way for you to make sure that when disaster strikes, you shrug it off as much as possible as “just another bump on the road of travel” is to make sure that everything you have is backed up. And not just once, but many times.
Luckily, it could not be easier now to make sure that everything you do is automagically synced to the cloud, usually has backup versions stored for months or years down the road, and can easily be restored in case of emergency.
Here’s how you make sure that you’re covered:
1 (Online) : Find an automatic online backup solution. This is an absolute must. If you only do one thing on this list, do this.
I’ve used backblaze for over 5 years now. It’s incredible. For what amounts to pennies a day, a tiny little program runs in the background of your computer and quietly backs up any new files every day to their secure servers.
The number of files you can back up is unlimited. For $5/month, you get to completely rest easy, never having to worry about sometime bad happening to your pictures, music, or sensitive documents. And you never even notice it running!
Seriously. Go sign up for a free 30 day trial right now. It will be the best digital-security based decision you’ve ever made!
And best of all? If you ever get your laptop stolen, you can simply download every single one of your old files whenever you get a replacement computer.
I had to do this once when I left that beautiful macbook air on the London tube…And I even have the files from computers that don’t even work anymore…they’re just waiting quietly on the cloud if I ever need to search for some file that I had from 2011, I can just login to backblaze.com and search for whatever file I want and download it.
This 1 change will help you relax so much about digital thievery. So the mental stress relieved is worth the minimal price.
2 (Offline): Backup your data to an external hard drive.
This one is pretty self-explanatory. And it’s somewhat old-school in the cloud era, but it’s always good to have offline copies of your data just in case the cloud based solutions.
As often as possible, you should back up your data to a hard drive, and then store it somewhere other than your home.
This is redundancy upon redundancy upon redundancy. Engineering and businesses build this type of thinking into their plans to mitigate losses, and you should too.
3 (Online) – Store your important files on Dropbox, and write your important notes on Evernote.
Dropbox and Evernote have many many virtues, but the one that is most relevant to our discussion of safety online is that they store your files or your notes automatically on the cloud. It’s effortless once you save a document to dropbox or save a note to evernote. You don’t have to think about it, it’s just backed up forever.
And definitely store important travel documents like passport copies and similar items in evernote or dropbox in case the actual thing gets stolen, you always have a copy on evernote or dropbox’s servers, which you can access online from any computer.
I recommend upgrading to the professional versions of both Dropbox and Evernote to fully enjoy the capabilities and full deliciously-redundant “version restore” capabilities of both to ease your mind.
4 (Online) – Keep track of your devices with Prey.
Prey is a handy little tool designed to let you keep track of your devices. It’s a tiny little app that runs silently on your computer or phone, and sends little signals back to secure servers every few minutes. It tracks the location of your computer or phone with gps or using wifi connections and even lets you perform some security measures if your devices get stolen or lost, like…
Find your stolen laptop or phone…
Disable it remotely…and “mark it as stolen”
Wipe your sensitive information off of the computer or phone…
And even take photos of whoever has stolen your laptop or phone secretly without their knowledge by remotely controlling the webcam or camera.
This is your last-resort best friend. If the worst happens and you lose your device, you can immediately log into prey from the web and tell it to lock, delete, and report the location of the device so you can use it for a police report, hopefully with the picture of a criminal for evidence!
Mac and iPhone have similar services with “Find my Mac” and “Find my iPhone” which you have to enable on your computer or phone, but once you do you can see a location of your device any time by logging in online.
When I lost my laptop in London, I immediately went to a friends computer, logged into where’s my mac, told it to delete everything the next time it connected to wifi, and I saw that it had been opened just a couple miles away…
Though there was little I could do about it.
Maybe if I would have had prey installed, I could have tried one of the other tactics.
This is a great little app to have “just in case”.
And it’s free: https://preyproject.com/download
If you do these 4 things, you will have created a web of redundant “fail safes” without much effort on your part so that in the worst case scenarios, you at least don’t fall behind too far, and if you do it correctly, you haven’t “lost” anything. And a chance at maybe even getting back your devices if they get stolen.
Now…onto the next step in the building of our digital fortress…
Step 3: Set Up Your Defense (Fortification)
Now for the nitty-gritty security steps.
I’ve focused on the easiest-to-implement, yet most impactful security “protocols” you can implement that will make it the least likely that someone will be able to crack, hack, or jack your laptop or phone.
This protocol is borrowed from futurist and crime prevention expert Marc Goodman. If you want to get a really great overview of the future of crime, check out mark’s Ted Talk:
https://www.ted.com/talks/marc_goodman_a_vision_of_crimes_in_the_future
Or his excellent interview with Tim Ferriss:
http://fourhourworkweek.com/2014/12/09/future-crimes/
Or check out his book “Future Crimes:”
http://www.futurecrimesbook.com/
Marc has spent many years analyzing the patterns of cyber crime and developed a simple system for significantly reducing your chances of being targeted for an attack. If you follow as many of these steps as you can, then you will reduce your likelihood of attack by 80 or 90%, and none of them require you to be a tech wizard or a paranoid security freak, they are mostly just simple tools or practices to follow that make it too much hassle for the average hacker or cyber-thief to bother with targeting you.
Without further adieu, Marc’s “Update” protocol:
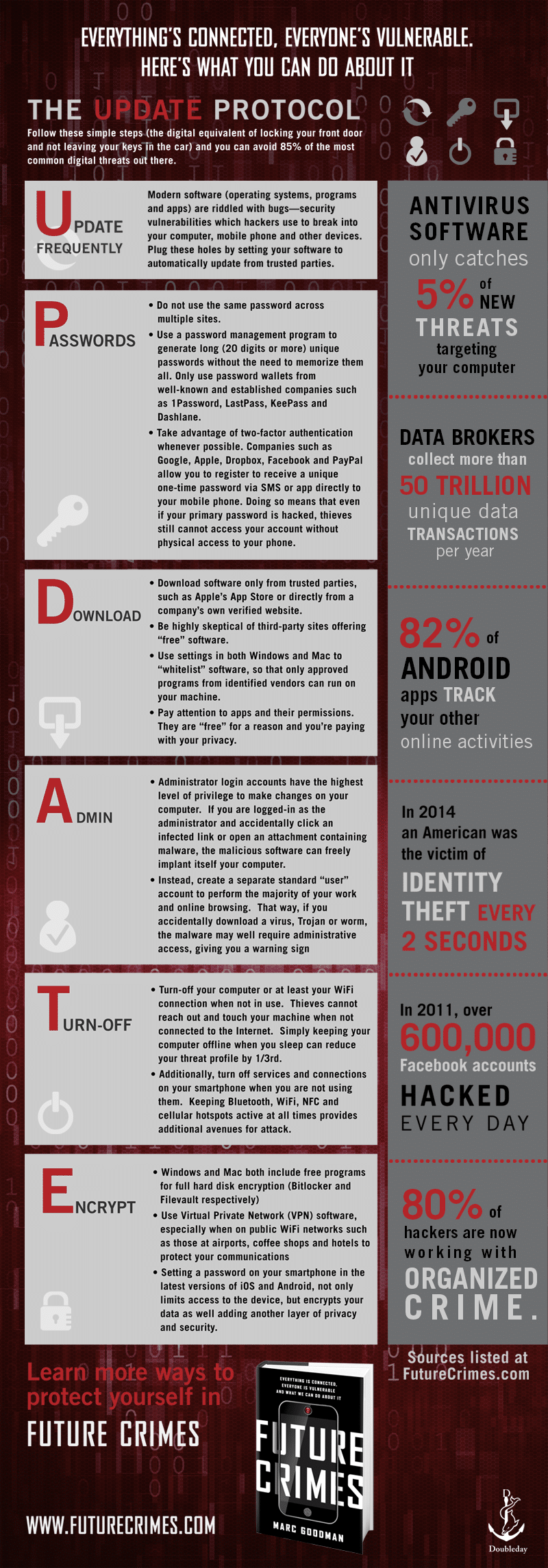
The U.P.D.A.T.E. Protocol for shielding yourself from cyber crime
U – Update frequently
This one is pretty self-explanatory. It’s simple, most computers and phones allow an “automatic updates” feature that you should promptly enable. There is a constant “Red Queen” battle going on between software developers and hackers and virus makers. You absolutely need to keep your operating system, apps, and mobile devices up to date at all times to protect yourself from hackers.
P – Passwords
Passwords are the most easy access point to most peoples’ devices, and it’s one of the simplest to solve with very little extra effort. One of the best, easiest ways to secure your passwords is to use a solution like Lastpass , which is what I use.
The idea behind last pass is that it’s the “Last Password” you ever need to remember. It stores all of your passwords for all of your websites, apps, and accounts behind a single password (which you should make sure is UNIQUE and VERY secure.)
How do you make a secure password? Here are the criteria (each one of these you add to your passwords makes it EXPONENTIALLY harder for hackers to crack your password). If someone REALLY wants to, it’s almost impossible to stop, but you can make it so difficult that it’s not worth their effort by using these simple techniques.
1) Make your password LONG (at least 20 digits)
2) Make sure your password includes at least one of the following:
– Upper case letter
– Lower case letter
– Number
– Symbol (@#,$,)
If you do these things, you will have a pretty un-hackable password. And if you use Lastpass, you don’t even have to remember it. Just make sure you remember your last pass password, and you’re set!
From my own experience however, that’s not how I use Lastpasss. I do have one, unique, secure password for Lastpass, and I do store all of my passwords in the lastpass cloud. It’s incredibly useful, you can access your passwords even when you’re not at the computer, and best of all…
If your stuff gets stolen or lost, you don’t lose your passwords. And you know that if you set up last pass correctly, and you follow the basic guidelines for last pass, even if someone has logged into your computer, they won’t be able to log into your websites.
For a website to measure how adding these different elements to your password multiples its security factor, check out http://www.passwordmeter.com/ (but don’t put in your real password…just play around with what adding these things will do).
D – Download
Basically, avoid sketchy “free” software, especially anti-virus software that is often masquerading as spyware. Don’t download from torrent sites (they’re basically the seedy underbelly of the internet). Just by going to these sites, you’re going to pick up all sorts of tracking cookies, popups, and lots of security threats.
There’s no free lunch! In the case of pirating movies and software, there is a cost…it’s usually your digital security and privacy. As often as possible, simply download apps from apple or verified microsoft software providers.
A – Admin
Instead of using your computer as an “Administrator” account that has ultimate access to make changes to deep system-level software, marc suggests simply creating a “normal user” account on your computer that should have plenty of access for doing the normal things you want to do, but if you accidentally download some sneaky software, it will have a much harder time accessing the most essential system files if it isn’t running around with your “Administrator” privileges.
Browsing around on the internet and downloading software while in Administrator mode is like keeping your door wide open all day and night with a sea of thieves and scoundrels wandering around outside. Don’t do it.
T – Turn Off
Turn off your computer and wifi when you’re not using it. According to marc, “simply keeping your computer offline while you sleep can reduce your threat profile by 1/3”. He also recommends turning off wifi and bluetooth on phones when they’re not being used.
E – Encrypt
To add another incredible amount of protection to your laptop and phone, you can simply turn on the data encryption programs included in Mac (FileVault) and Windows (Bitlocker) operating systems. These programs are free and built into the operating systems, they simply need to be turned on. And they each help to reduce access to the data on your device by scrambling the data on your hard drive until you log in (with your new non-admin user account, and your super-strong password after reading this article).
To do the same signal-scrambling magic to the information that’s being sent to and from your computer over public wifi networks, you will want to use a simple VPN solution while you’re using particularly public wifi sources, which can often be very un-secure (even if they have a password).
Especially necessary in coffee shops and airports. I prefer Cloak VPN . It’s simply, it doesn’t take ANY tech knowledge whatsoever. You just turn it on, and it secures the data that comes to and from your computer over your wifi by running it through their own secure servers (or some such fancy techno-babble). They offer cloak for mac and iOS.
I have no experience with Windows apps, but here’s a blog post about the top Windows VPN Clients.
(Let me google that for you… haha )
Usually when you’re on your home wifi you don’t need to use a VPN but I always turn on cloak when I’m working from a cafe or at an airport.
If you follow Marc’s UPDATE protocol, you should reduce your risk of any sort of privacy invasion by 80 or 90%. Each piece you add to your digital armory increases your security exponentially, so don’t worry if you can’t/don’t have time to/ or don’t understand how to do all of them. Just pick as many as you can and implement them today!
Now that you’ve prepared by pre-mourning and letting go…
And mitigated any potential losses by creating a web of redundant backups…
And you’ve put your defense systems in place, fortifying your devices…
If you remember the 3 steps to secure your laptop and phone while traveling…
What were they again?
That’s right…
Preparation, Redundancy, and Fortification…
You should be relatively shielded from the bad guys while you wander around the world wide web. Now you can relax a bit, rest assured and focus on going forth, experiencing the world and sharing what you discover with those who will benefit from it.
Stay Safe,
Brad
Resources:
Information:
Marc Goodman – Future Crimes Book
Marc Goodman – Ted Talk – “A vision of crimes in the future”
Marc Goodman – Interview with Tim Ferriss “Marc Goodman, FBI Futurist, on High-Tech Crime and How to Protect Yourself”
Software:





